< Using Nmap and Wireshark in a Lab Setting >
Exploring Cybersecurity: A Student’s Journey Through Network Analysis and Vigilance
From what I have heard about cybersecurity, practical skills are just as vital as academic learning. My journey through the “Emerging Technologies in Cybersecurity – C844” course at WGU has deepened my appreciation for this field, presenting challenges that honed my analytical and research abilities and further solidified my enthusiasm for cybersecurity.
Grasping Network Structures with Zenmap
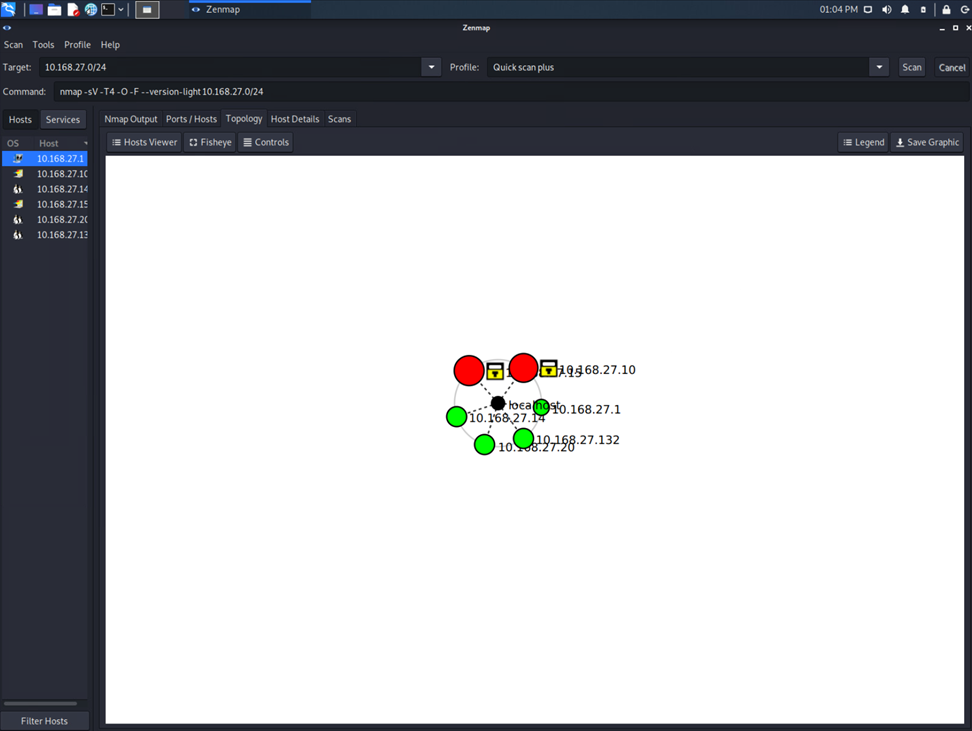
One of our initial tasks was to figure out the network’s structure, which is crucial for any security assessment. I used Zenmap, a user-friendly graphical interface for the network mapping tool Nmap. It helped identify the network’s “star topology.” In a star topology, all network devices are connected to a single central device. While this setup can be efficient, it also means that if the central device fails, the entire network can go down.
The way Zenmap displayed this information was not only clear but also highlighted the thoughtful design of the software, making complex data easy to understand.
Uncovering Security Flaws
Our scans identified several security issues:
Some Windows computers were vulnerable to a well-known vulnerability called Eternal Blue because their operating systems were outdated. This vulnerability could allow attackers full control of the system with the press of a button.
A few devices were running on an old Linux kernel, making them targets for numerous security threats, such as stack-based buffer overflows.
An outdated version of OpenSSH could potentially leak sensitive information.
These findings emphasized the need for ongoing vigilance and regular software updates to protect against cyber threats.
Analyzing Network Traffic with Wireshark
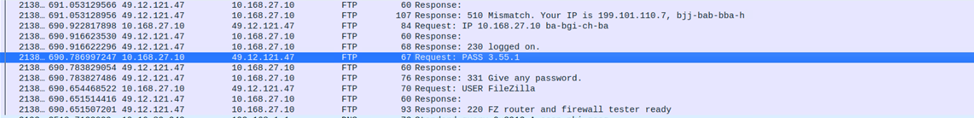
Wireshark allows us to see the data flowing through the network—like watching the bloodstream of the internet. We uncovered some alarming activities:
Unauthorized scans of our network ports, could indicate hackers trying to find a way in.
An FTP (File Transfer Protocol) session was sending usernames and passwords in plain text, which is risky because anyone who intercepts this data can read it easily.
Wireshark taught me how to spot these digital traces of nefarious activities, a critical skill for anyone in cybersecurity.
Facing and Overcoming Technical Challenges
One major challenge was figuring out which software versions were unsafe. I spent a lot of time researching, often turning to Google for information. In some instances, I needed extra help interpreting the data from Wireshark, which I found through resources like ChatGPT. These experiences reminded me that while technology gives us data, interpreting that data often requires human insight.
Reflections on the Project and Looking Ahead
This project was very fun for me. It was a practical demonstration of the theories we learned in class, showing the complexities of network security in the real world. Although this may be an unpopular opinion, I favored Zenmap over Nmap in this case due to how beautifully it laid out the network topology.
As I move toward a career in cybersecurity, I take with me not just the skills to use tools like Zenmap and Wireshark, but an understanding of their strategic importance. This project has prepared me for future challenges, shaping how I will tackle problem-solving and manage vulnerabilities in my professional life.
Conclusion
The “Emerging Technologies in Cybersecurity – C844” course was more than just an academic task; it was a deep dive into the practical realities of the field. As I finished this project, I thought about how much more fun it would be to do this for real without paying tuition.
References used in the project
Penetration Testing Writeup: “Active” (Retired Machine…
< Penetration Testing Writeup: “Active” (Retired Machine from HackTheBox)> Executive Summary This report summarizes a penetration test conducted against a Windows Active Directory environment. The testing identified critical vulnerabilities including the storage of administrative credentials…
My Methodology for Passing Any Certification…
My Methodology for Passing Any Certification in Under 2 Months Hello! I wanted to share my methodology for earning certifications and learning efficiently without sacrificing quality. Over the years, I’ve developed a system that helps…
Cloud Honeypot Setup with Azure Sentinel
< Step-by-Step Guide: Cloud Honeypot Setup with Azure Sentinel> Introduction In this project, I set up a vulnerable virtual machine (VM) in Microsoft Azure, configured it to log failed Remote Desktop Protocol (RDP) login attempts,…